Introduction: Why is Cybersecurity Important?
In today’s digital age, everything from our bank accounts to personal photos and health records is online. All this information is a potential target for cyber attackers. This is where cybersecurity comes in. So, what does it mean to keep a system or data secure? The answer lies in the CIA Triad, the most fundamental building block of cybersecurity.
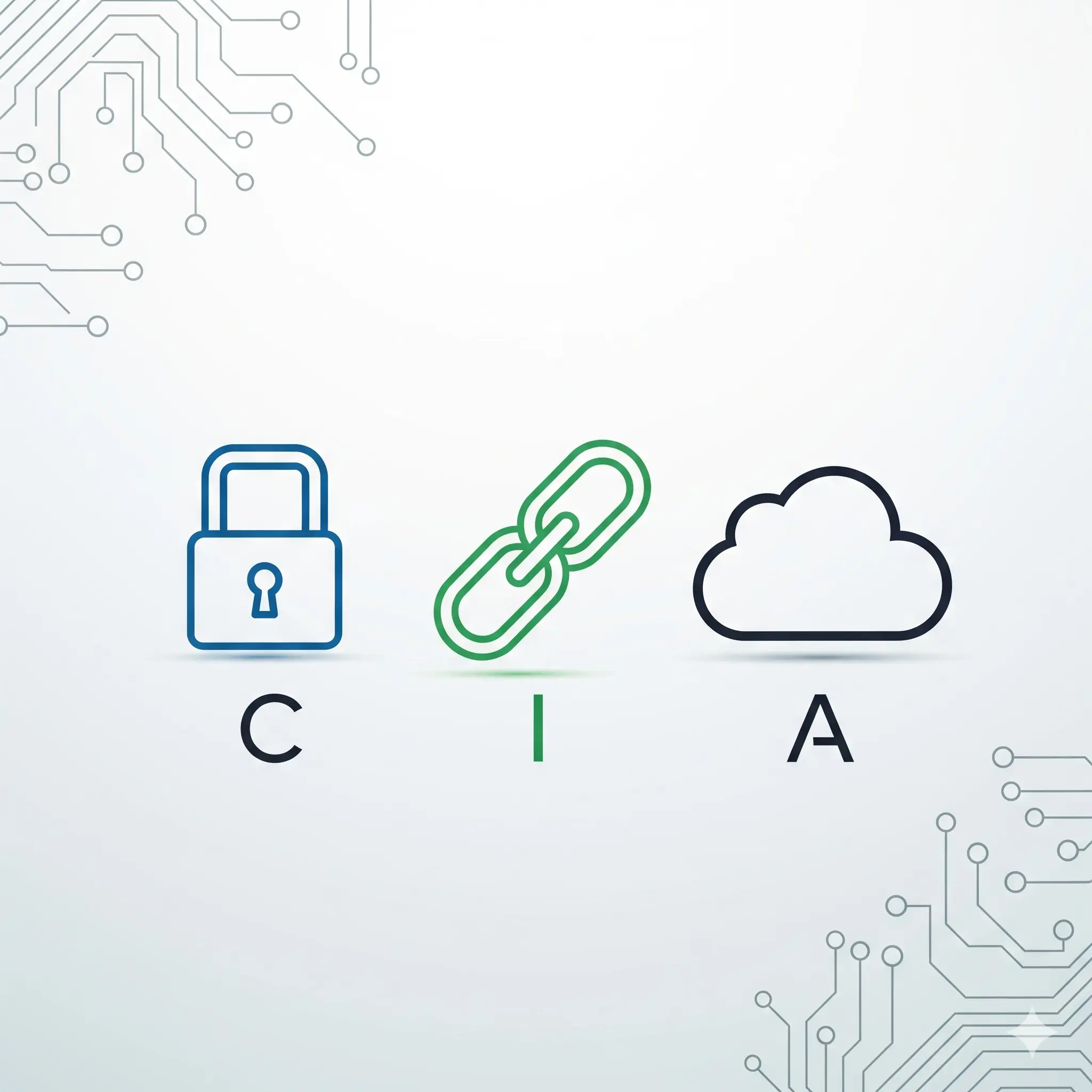
What is the CIA Triad?
The CIA triad is an acronym for the three core principles used to ensure information security: Confidentiality, Integrity, and Availability. Let’s explore each concept.
1. Confidentiality
Confidentiality is about preventing sensitive information from falling into the wrong hands. Just like a letter that only the recipient can open, confidentiality ensures that data is only viewable by authorized users.
- Example: Logging into your email account with a password; your bank account being private to you.
- Violation Example: A hacker stealing user passwords from a database.
2. Integrity
Integrity is about preventing unauthorized or accidental modification, deletion, or corruption of data. It ensures that the data is accurate and trustworthy.
- Example: On an e-commerce site, your order is accurately listed with the correct products and order number.
- Violation Example: An attacker changing the amount of money in your bank account without your permission.
3. Availability
Availability ensures that authorized users can access systems and data when needed. This includes a website being accessible 24/7 or a file being retrievable at any moment.
- Example: A website providing uninterrupted service around the clock.
- Violation Example: A website crashing due to a cyberattack (DDoS), preventing users from accessing it.
Why is it So Important?
A cyberattack often targets one or more of these three principles. For example, an attack on a bank’s database could violate Confidentiality by stealing customer information and Integrity by changing account balances.
The CIA triad acts as a guiding compass when designing a system or analyzing a security breach.
What’s next?
In our upcoming posts, we’ll dive into the methods and tools used to protect these fundamental principles. Get ready to join me on this journey!
Related Posts: