
The Black Screen: I Formatted Everything and Now I'm Lost
Surviving the first few minutes of a pure text-based Linux experience.

Surviving the first few minutes of a pure text-based Linux experience.

The Next Step in Your Cybersecurity Journey In our last post, we discussed the CIA Triad, the foundation of cybersecurity. Now, we’ll examine how these fundamental principles are violated by the most common types of cyber attacks. Just as a security guard knows where threats can come from, understanding our enemies in the digital world is the first step to protecting ourselves. 1. Phishing: The Most Common Form of Social Engineering Phishing is a social engineering tactic where cyber attackers try to trick you into revealing personal information (passwords, credit card numbers, etc.) through deceptive emails, messages, or websites. ...
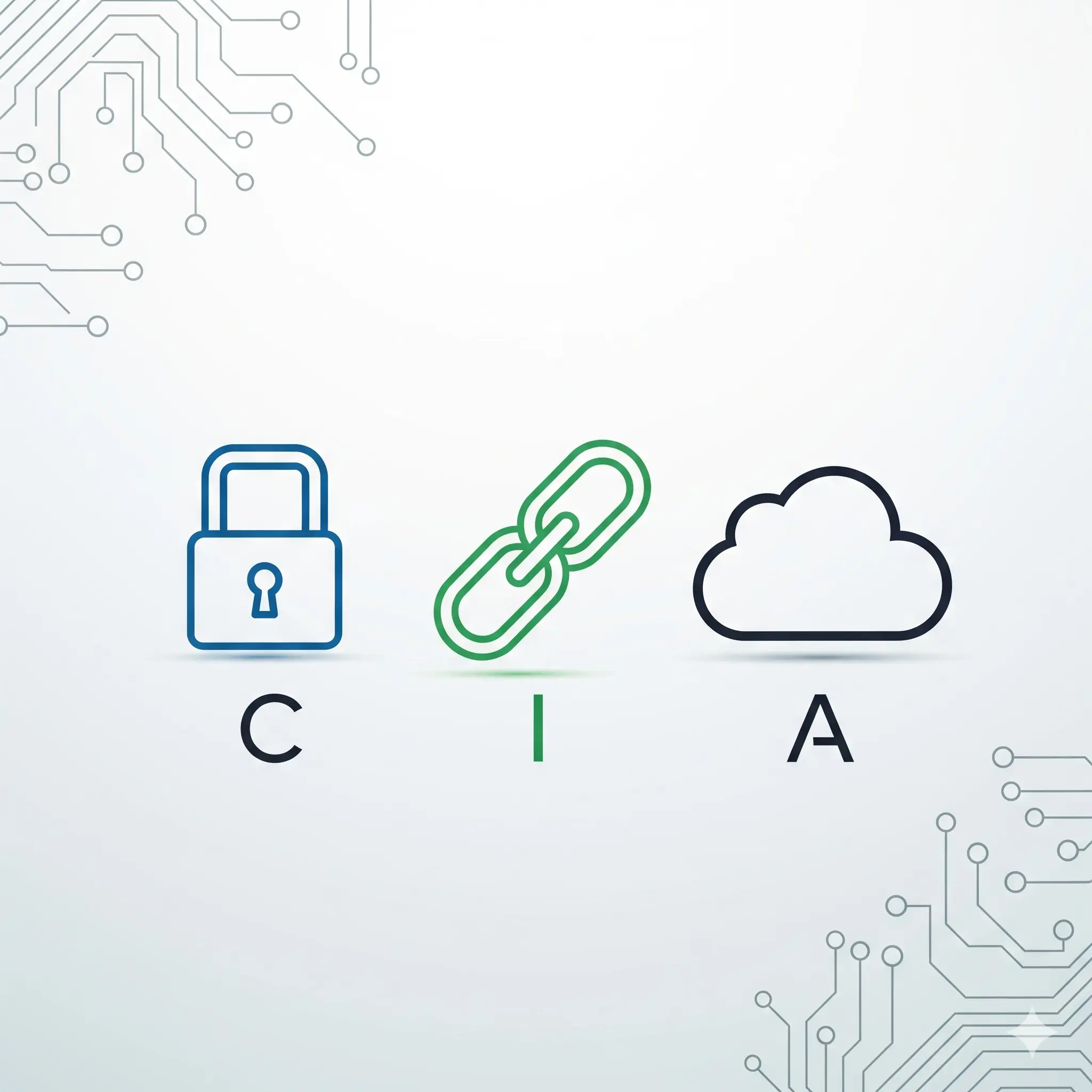
Learn about the three core principles of cybersecurity: Confidentiality, Integrity, and Availability. This guide covers why they are crucial with simple examples.